Crypto Cracker: Cryptocurrency Security in 2024

Crypto Cracker: Cryptocurrencies have surged in popularity since the advent of Bitcoin in 2009, evolving from niche technology to a mainstream financial asset. However, as the value and adoption of cryptocurrencies have grown, so too has cybercriminals’ interest. The concept of a “crypto cracker”—someone who uses their skills to break into cryptocurrency wallets, exchanges, or networks—has become increasingly relevant. In 2024, the landscape of cryptocurrency security will be more complex and difficult than ever.
The Rise of Crypto Cracking
Crypto cracking refers to the unauthorized access and theft of cryptocurrency, including exploiting vulnerabilities in blockchain protocols, cracking cryptographic keys, and hacking into exchanges or wallets. This illicit activity has grown in parallel with the cryptocurrency market, driven by the lucrative potential of digital assets.
In the early days of cryptocurrency, cracking often involved simple tactics like phishing, where attackers trick users into revealing their private keys or passwords. As the industry matured, so did the methods of attack. Today, crypto crackers employ sophisticated techniques, including brute-force attacks on encryption, exploiting smart contract vulnerabilities, and even launching coordinated attacks on blockchain networks.
Major Incidents in Recent Years
Several high-profile incidents in recent years have highlighted the growing threat of crypto cracking. One of the most significant was the 2022 attack on the Ronin Network, a blockchain used for the popular Axie Infinity game. Hackers exploited a vulnerability in the network’s validator nodes to steal over $600 million worth of cryptocurrency. This attack was a stark reminder of the vulnerabilities of even the most well-established blockchain networks.
Another notable case was the 2023 breach of the cryptocurrency exchange BitMart. Hackers used a technique known as a “supply chain attack” to infiltrate the exchange’s software, eventually siphoning off nearly $200 million in various cryptocurrencies. These incidents underscore the growing sophistication of crypto crackers and the need for enhanced security measures across the industry.
Evolving Tactics: From Brute Force to Social Engineering
The methods used by crypto crackers have evolved significantly over the years. While brute-force attacks on cryptographic keys remain a concern, they are less common due to the increasing complexity of encryption algorithms. Today, attackers often rely on a combination of tactics to achieve their goals.
Social Engineering
Social engineering has become one of the most effective tools in the crypto cracker’s arsenal. Attackers can access wallets, accounts, or private keys by manipulating individuals into divulging sensitive information. This can include phishing emails that appear legitimate, fake customer support calls, or even impersonating friends or colleagues on social media. The human element remains one of the weakest links in the security chain.
Smart Contract Exploits
As decentralized finance (DeFi) platforms have grown, so too have the number of smart contract exploits. Smart contracts, which are self-executing contracts with the terms of the agreement directly written into code, are particularly vulnerable to bugs and vulnerabilities. Crypto crackers often target these weaknesses to drain funds from DeFi platforms or manipulate markets.
51% Attacks
Another growing threat is the 51% attack, where an attacker gains control of most of a blockchain’s hashing power. This allows them to alter the blockchain’s ledger, potentially reversing transactions or double-spending coins. While larger networks like Bitcoin and Ethereum are less susceptible due to their vast hashing power, smaller networks remain at risk.
The Role of Quantum Computing
One of the looming threats on the horizon for cryptocurrency security is quantum computing. While still in its early stages, quantum computing has the potential to break the cryptographic algorithms that underpin most cryptocurrencies. Traditional encryption methods, such as RSA and elliptic curve cryptography, rely on the difficulty of factoring large numbers or solving discrete logarithm problems—tasks that quantum computers could theoretically perform much more efficiently.
The cryptocurrency community has begun exploring quantum-resistant algorithms in response to this potential threat. These are designed to withstand the computing power of quantum machines, but widespread adoption and implementation remain years away. For now, quantum computing serves as a reminder of the ever-evolving nature of crypto security challenges.
Defensive Measures: Staying Ahead of Crypto Crackers
Given the increasing sophistication of crypto crackers, the need for robust security measures has never been greater. Individuals, exchanges, and developers all play a role in maintaining the security of the cryptocurrency ecosystem.
Multi-Factor Authentication (MFA)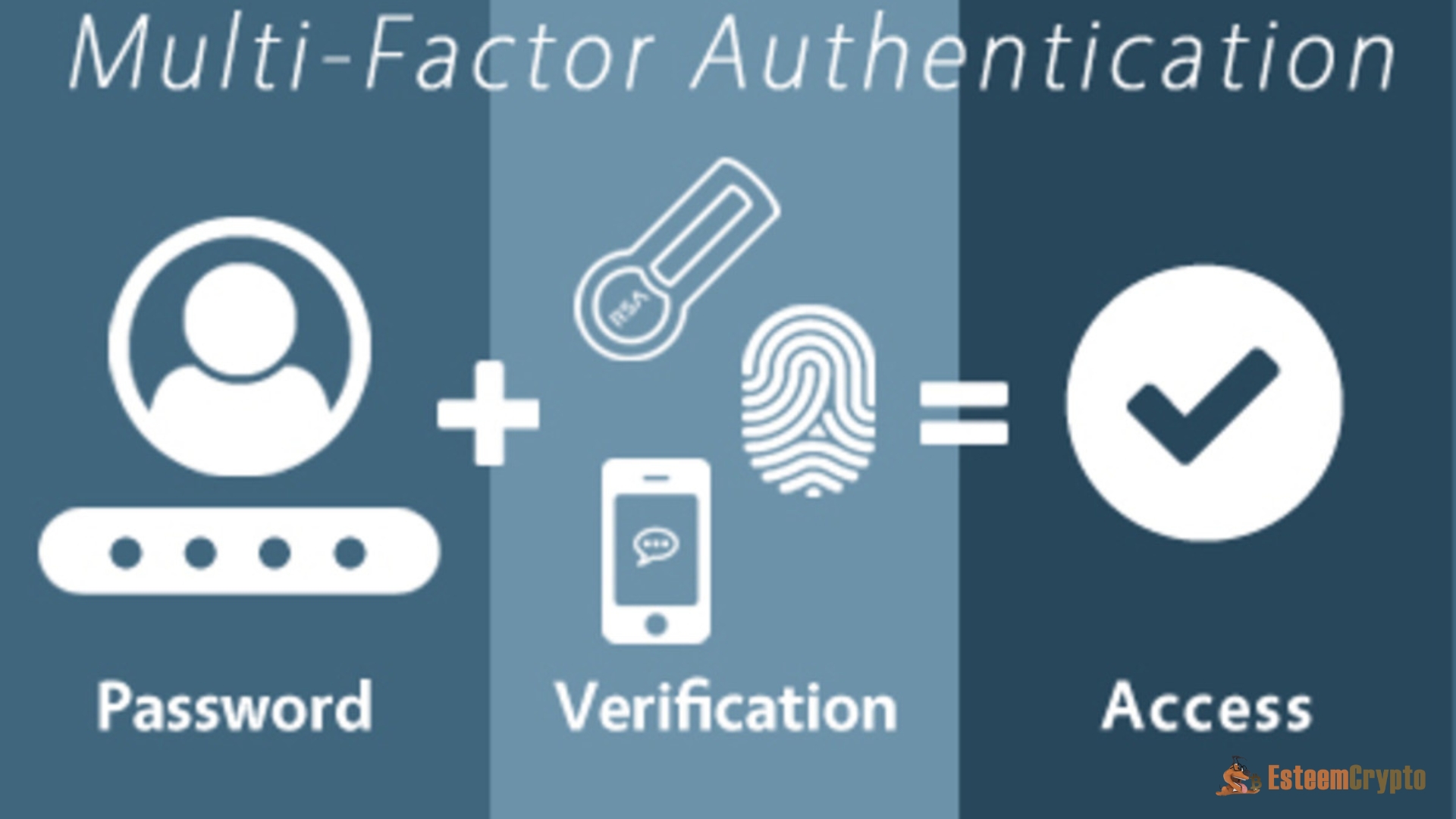
One of the simplest yet most effective security measures is multi-factor authentication. MFA adds a layer of security that can thwart many common attacks by requiring multiple forms of verification (e.g., a password and a code sent to a mobile device).
Hardware Wallets
For individual users, hardware wallets offer one of the most secure ways to store cryptocurrencies. These physical devices store private keys offline, making them immune to many forms of online attacks. However, they must be used carefully, as losing the device or forgetting the associated recovery phrase can permanently cause you to lose funds.
Auditing and Code Reviews
Developers must regularly audit and review code. Many crypto cracking incidents stem from vulnerabilities in smart contracts or other software. By conducting thorough audits, developers can identify and fix potential issues before attackers exploit them.
Decentralized Security Models
Decentralization, a core principle of blockchain technology, can also enhance security. By distributing control and decision-making across a network, decentralized systems are less susceptible to single points of failure. However, decentralization comes with challenges, particularly in governance and coordination.
The Future of Crypto Cracking
As cryptocurrency becomes more widely used, crypto crackers and security specialists will face an uphill struggle. Combining modern technology, like quantum-resistant cryptography, with old-fashioned attentiveness, such as user education and best practices, will likely be the future of cryptocurrency security.
Possible progress includes the emergence of security technologies powered by AI. These may monitor blockchain networks in real-time, looking for suspicious activities and reacting to any dangers before they cause serious harm. Furthermore, when cryptocurrency legislation is clarified, platforms and exchanges may be compelled to establish more rigorous security protocols.
Finally, crypto crackers are a genuine and increasing concern, but the industry has countermeasures. The Bitcoin ecosystem can be better protected against the constant cybercrime risk if users and developers keep themselves informed and follow best practices. We must adapt our plans for protecting digital assets to the ever-changing crypto security landscape.